A recent investigation has unveiled a cybercriminal operating out of Mexico who is responsible for a widespread Android mobile malware campaign. This individual Mexican Hackers band, known as Neo_Net, has been specifically targeting financial institutions worldwide, with a particular focus on Spanish and Chilean banks. The research was conducted by security expert Pol Thill in collaboration with vx-underground and published by SentinelOne.
The Mexican Hackers Neo_Net Tactics
Despite utilizing relatively simplistic tools, Neo_Net has achieved remarkable success by tailoring their infrastructure to suit specific targets. Their activities have resulted in the theft of over 350,000 EUR from victims’ bank accounts and compromising Personally Identifiable Information (PII) belonging to thousands of individuals.
The Mexican Hackers Neo_Net Major Targets
Neo_Net’s primary targets include renowned banks such as Santander, BBVA, CaixaBank, Deutsche Bank, Crédit Agricole, and ING. These financial institutions have fallen victim to the hacker’s sophisticated attacks.
Cybercrime Expertise of Neo_Net
Neo_Net has established themselves as an experienced cybercriminal within the Spanish-speaking community residing in Mexico. They are involved in various illicit activities including selling phishing panels and compromised data to third parties. Additionally, they offer “Ankarex,” a smishing-as-a-service platform designed to target multiple countries globally.
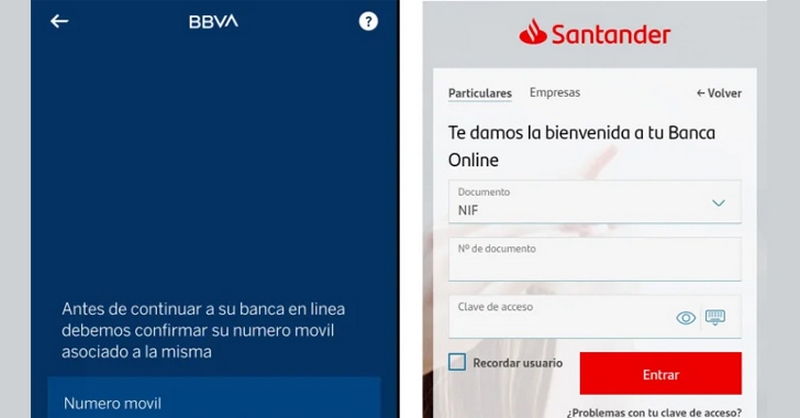
SMS Phishing: Initial Entry Point
The attack begins with SMS phishing techniques employed by the threat actor. Through manipulative scare tactics via text messages, unsuspecting recipients are lured into clicking on fraudulent landing pages that mimic legitimate banking applications. By utilizing a Telegram bot system during this phase of the attack process allows for harvesting and exfiltrating victims’ credentials seamlessly.
Meticulously Crafted Phishing Pages
Neo_Net takes great care when setting up their phishing pages using dedicated panels like PRIV8 along with implementing multiple defense measures. These precautions include blocking requests from non-mobile user agents and concealing the pages from bots and network scanners. The result is a convincing replica of genuine banking applications, complete with animations to deceive victims effectively.
Rogue Android Apps Exploiting Security Software
In addition to SMS phishing, Neo_Net has been observed tricking bank customers into installing rogue Android apps disguised as security software. Once installed, these malicious apps request SMS permissions to intercept two-factor authentication (2FA) codes sent by banks. This allows the hacker to gain unauthorized access to victims’ accounts.
Ankarex: Smishing-as-a-Service Platform
Neo_Net’s Ankarex platform has been active since May 2022 and is actively promoted on a Telegram channel boasting approximately 1,700 subscribers. Users can register on ankarex[.]net and upload funds using cryptocurrency transfers. With this service, individuals can launch their own smishing campaigns by specifying the content of SMS messages and target phone numbers.
Anatsa Banking Trojan Campaign
Coinciding with these developments, ThreatFabric recently revealed details about an ongoing Anatsa (aka TeaBot) banking trojan campaign that specifically targets customers in the U.S., U.K., Germany, Austria, and Switzerland since March 2023.
In conclusion, cybercriminal activities carried out by Neo_Net have posed significant threats to global financial institutions. Their sophisticated tactics in targeting Spanish and Chilean banks highlight the need for enhanced cybersecurity measures within the banking sector at large.
Learn here more about Cybersecurity and Privacy.
You can also reach out our social media team by following our pages on Facebook, Instagram and Twitter.